一.简介
在实际使用中更多的是配置 HTTPS 等安全的外部访问。例如,在这个场景中,将网格内的 HTTPS 服务通过 HTTPS 协议发布。这样在浏览器端中输入“https://weather.com”就可以访问到这个服务
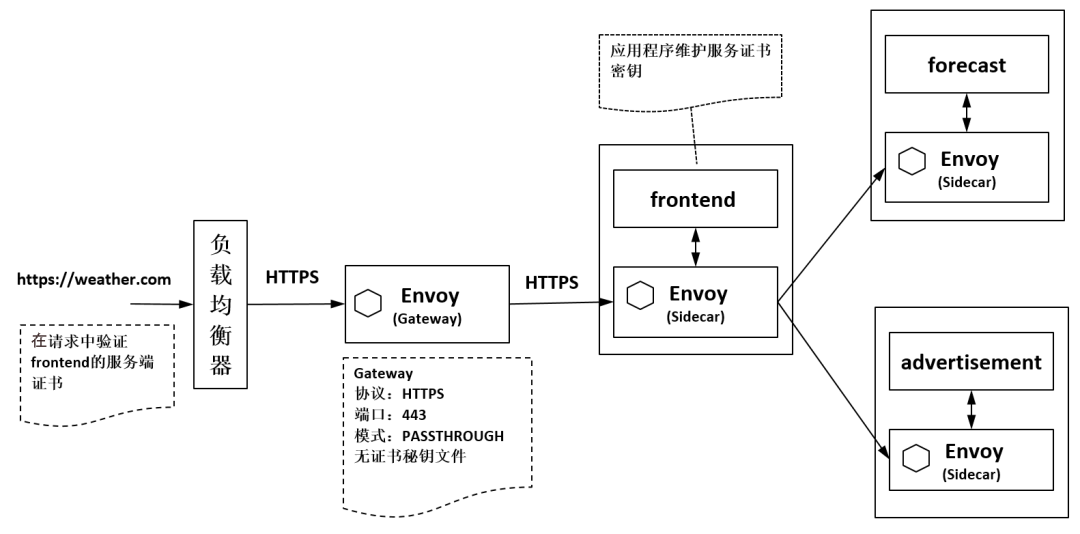
二.配置
1.体系结构
对比k8s ingress-nginx
gateway-controller <-> ingress-controller (实际的pod)
istio-ingressgateway <-> nginx-ingress-controller (一种实现)
gateway <-> ingress (配置)
2.配置Gateway
如果需要istio-ingressgateway作为外网的访问入口,就需要将Gateway的网络设置为hostNetwork
需要添加一下两个配置
dnsPolicy: ClusterFirstWithHostNet
hostNetwork: true
设置完成后有一个问题需要处理,默认情况下Gateway监听的端口是8080和8443,如果对外提供服务的话需要使用iptables将入口的80和443流量转发到8080和8443
iptables -t nat -A PREROUTING -p tcp --dport 443 -j REDIRECT --to-port 8443
iptables -t nat -A PREROUTING -p tcp --dport 80 -j REDIRECT --to-port 8080
这样配置还有个缺点,就是控制器是deploy,如果重启迁移到其他的节点的话,如果没有iptables规则,就无法访问了
所以建议使用nodeName: k8s-nacos-001 限制调度到指定节点,或者将deploy修改为ds
配置完成后可以查看本地监听是否正常
netstat -anpt | grep -w 8443
tcp 0 0 0.0.0.0:8443 0.0.0.0:* LISTEN 11965/envoy
tcp 0 0 172.24.3.99:8443 123.52.19.50:51796 ESTABLISHED 11965/envoy
tcp 0 0 172.24.3.99:8443 123.52.19.50:52967 ESTABLISHED 11965/envoy
netstat -anpt | grep -w 8080
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 11965/envoy
tcp 0 0 172.24.3.99:8080 1.193.82.222:6698 ESTABLISHED 11965/envoy
tcp 0 0 172.24.3.99:8080 1.193.82.222:6750 ESTABLISHED 11965/envoy
3.配置服务通过Gateway
以nginx为例
# Gateway配置
apiVersion: networking.istio.io/v1beta1
kind: Gateway
metadata:
name: nginx-http-gateway
spec:
selector:
istio: ingressgateway
servers:
- hosts:
- www.huhuhahei.cn
port:
name: nginx
number: 80
protocol: HTTP
---
#VirtualService配置
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:
name: nginx-http-vs
spec:
gateways:
- nginx-http-gateway
hosts:
- www.huhuhahei.cn
http:
- name: nginx
route:
- destination:
host: nginx-php.default.svc.cluster.local
port:
number: 80
weight: 100
---
#DestinationRule配置
#DestinationRule配置
apiVersion: networking.istio.io/v1beta1
kind: DestinationRule
metadata:
name: kode
namespace: default
spec:
host: kode.default.svc.cluster.local
trafficPolicy:
portLevelSettings:
- port:
number: 80
tls:
mode: DISABLE
4.配置https访问
添加证书到Gateway
kubectl create -n istio-system secret tls istio-ingressgateway-certs --key private.key --cert public.pem
在IngressGateway中查看证书是否添加成功
kubectl exec -it -n istio-system $(kubectl -n istio-system get pods -l istio=ingressgateway -o jsonpath='{.items[0].metadata.name}') -- ls -al /etc/istio/ingressgateway-certs
drwxrwsrwt 3 root istio-proxy 120 May 21 10:53 .
drwxr-xr-x 1 root root 4096 May 21 10:53 ..
drwxr-sr-x 2 root istio-proxy 80 May 21 10:53 ..2022_05_21_10_53_29.239795056
lrwxrwxrwx 1 root root 31 May 21 10:53 ..data -> ..2022_05_21_10_53_29.239795056
lrwxrwxrwx 1 root root 14 May 21 10:53 tls.crt -> ..data/tls.crt
lrwxrwxrwx 1 root root 14 May 21 10:53 tls.key -> ..data/tls.key
Gateway中配置证书
#Gateway
apiVersion: networking.istio.io/v1beta1
kind: Gateway
metadata:
name: nginx-gateway
namespace: default
spec:
selector:
istio: ingressgateway
servers:
- hosts:
- www.huhuhahei.cn
port:
name: nginx
number: 443
protocol: HTTPS
tls:
mode: SIMPLE
privateKey: /etc/istio/ingressgateway-certs/tls.key
serverCertificate: /etc/istio/ingressgateway-certs/tls.crt
---
#VS
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:
name: nginx-vs
namespace: default
spec:
gateways:
- nginx-gateway
hosts:
- www.huhuhahei.cn
http:
- name: nginx
route:
- destination:
host: nginx-php.default.svc.cluster.local
port:
number: 80
weight: 100
这样域名http和https都可以访问
二.Gateway配置详解
1.配置http强制调整https
kind: Gateway
apiVersion: networking.istio.io/v1alpha3
metadata:
name: nginx-gateway
namespace: default
spec:
servers:
- port:
number: 443
protocol: HTTPS
name: nginx-https
hosts:
- www.huhuhahei.cn
tls:
mode: SIMPLE
serverCertificate: /etc/istio/ingressgateway-certs/tls.crt
privateKey: /etc/istio/ingressgateway-certs/tls.key
- port:
number: 80
protocol: HTTP
name: nginx-http
hosts:
- www.huhuhahei.cn
tls:
httpsRedirect: true # 301http跳转https
selector:
istio: ingressgateway



