一、配置etcd证书到prometheus
对于 etcd 集群一般情况下,为了安全都会开启 https 证书认证的方式,所以要想让 Prometheus 访问到 etcd 集群的监控数据,就需要提供相应的证书校验。这里配置的是kubeadm
查看证书文件位置
[root@master servicemonitor]# kubectl get pod etcd-master -n kube-system -o yaml
......
volumeMounts:
- mountPath: /var/lib/etcd
name: etcd-data
- mountPath: /etc/kubernetes/pki/etcd
name: etcd-certs
可以看到etcd-certs挂载路径是/etc/kubernetes/pki/etcd
获取证书文件后生成secret 挂载到pormetheus
kubectl -n monitoring create secret generic etcd-certs --from-file=/etc/kubernetes/pki/etcd/healthcheck-client.crt --from-file=/etc/kubernetes/pki/etcd/healthcheck-client.key --from-file=/etc/kubernetes/pki/etcd/ca.crt
二、配置prometheus
[root@master servicemonitor]# kubectl -n monitoring edit prometheus k8s
#spec添加下面字段
spec
......
secrets:
- etcd-certs
#保存退出 进入prometheus确认证书是否配置成功
[root@master servicemonitor]# kubectl -n monitoring exec -it prometheus-k8s-0 -c prometheus -- sh
/prometheus $ ls /etc/prometheus/secrets/etcd-certs/
ca.crt healthcheck-client.crt healthcheck-client.key
#证书已经配置成功
三、创建ServiceMonitor
ServiceMonitor
apiVersion: monitoring.coreos.com/v1
kind: ServiceMonitor
metadata:
name: etcd-k8s
namespace: monitoring
labels:
k8s-app: etcd-k8s
spec:
jobLabel: k8s-app
endpoints:
- port: port
interval: 30s
scheme: https
tlsConfig:
caFile: /etc/prometheus/secrets/etcd-certs/ca.crt
certFile: /etc/prometheus/secrets/etcd-certs/healthcheck-client.crt
keyFile: /etc/prometheus/secrets/etcd-certs/healthcheck-client.key
insecureSkipVerify: true
selector:
matchLabels:
k8s-app: etcd
namespaceSelector:
matchNames:
- kube-system
server
apiVersion: v1
kind: Service
metadata:
name: etcd-k8s
namespace: kube-system
labels:
k8s-app: etcd
spec:
type: ClusterIP
clusterIP: None
ports:
- name: port
port: 2379
protocol: TCP
---
apiVersion: v1
kind: Endpoints
metadata:
name: etcd-k8s
namespace: kube-system
labels:
k8s-app: etcd
subsets:
- addresses:
- ip: 10.46.8.18
nodeName: etcd-master
ports:
- name: port
port: 2379
protocol: TCP
apply
[root@master servicemonitor]# kubectl apply -f etcd_servicemonitor.yaml
[root@master servicemonitor]# kubectl apply -f etcdService.yaml
可以查看prometheus中监控已经有了 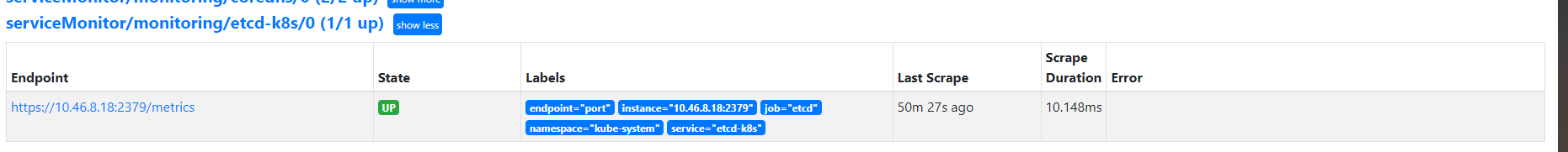
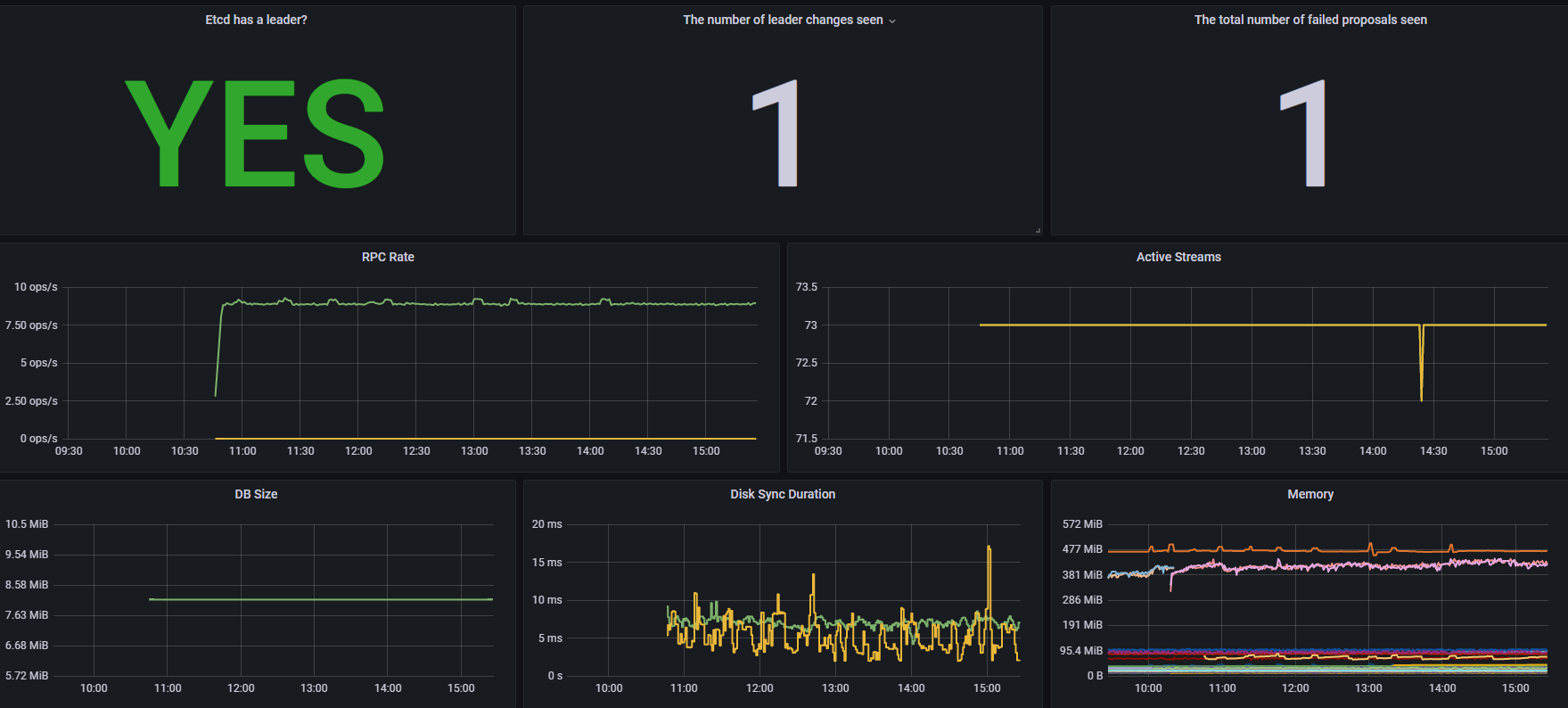
grafana添加监控 模板3070 效果如下